
Security investments are typically made in preventing an attack and exfiltration.
This leaves a giant blind spot for organizations as attackers that bypass the perimeter can then move laterally and steal credentials as they quietly establish a foothold, gain privileges, and recon the network in search of their targets.
Threats arise from in a variety of factors and can come in the form of external threat actors.
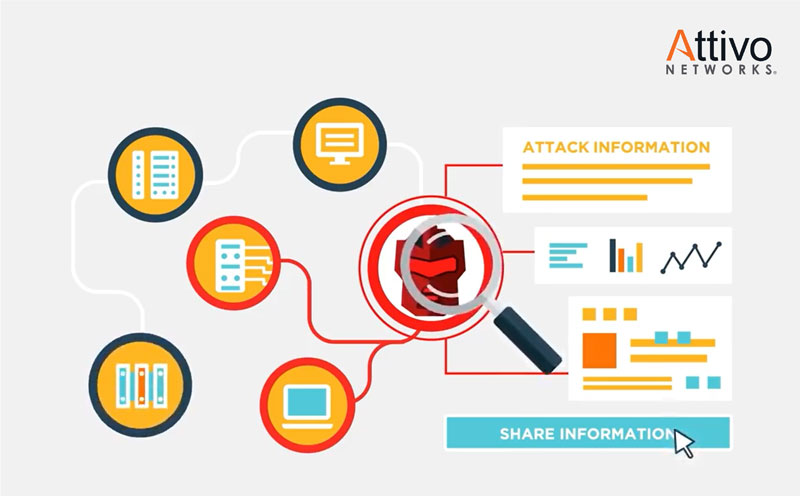
Knowing that an attacker is operating inside your network is valuable.However, knowing an attacker’s methods and gaining the threat intelligence to shut down current attacks and prevent future attacks, provides the empowerment to truly defend your networks and data centers. (Courtesy of Attivo Networks)




























